
Gain Early Access to Precise Attack Intelligence
Early Detection
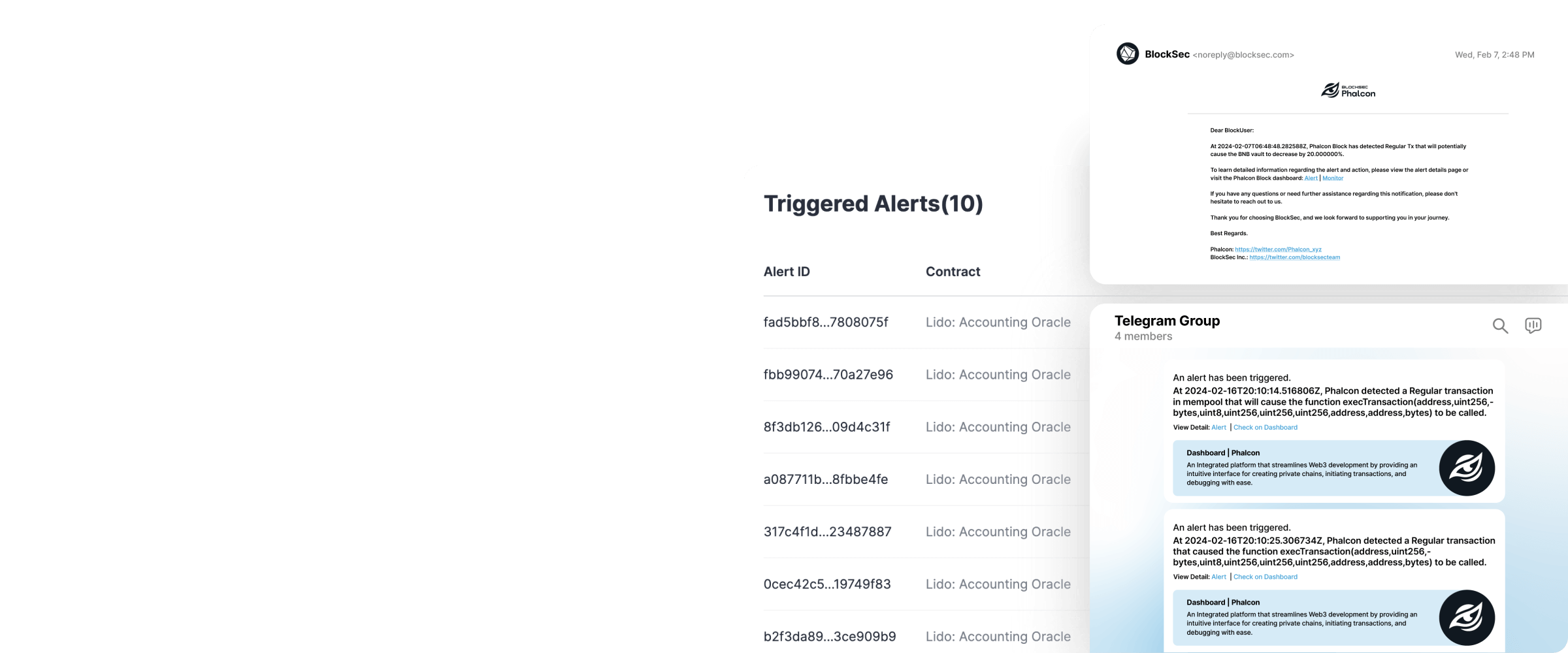
Cover Mempool and on-chain transactions, monitor for malicious proposals and contracts, and more.

Precise Detection
Leverage DeFi semantics and AI algorithms to achieve high precision.

Automated Attack Blocking with Customized Actions
Automated Actions
Implement swift and automatic responses to threats.

Multi-Signature Support
Enable automated actions with multi-signature wallets.

Transaction Sending Strategy
Utilize private RPC, gas bidding, and set gas price limits to counteract attacks.

No-Code, Flexible Monitoring Rules Configuration
Ease of Use
Monitor transactions, functions, events, and variables easily without the need for coding.

Pre-Set Templates
Access a variety of monitoring templates covering major security issues for protocols including Lending, DEX, Restaking, Liquid Staking, etc.

Meet Both Security and Operational Monitoring Requirements
Comprehensive Monitoring
Keep an eye on changes to admin keys, role grants, key variables, contract upgrades, time lock, new proposals and price oracles.
Diverse Notification Channels
Receive alerts through multiple channels including webhooks, Telegram, Slack, email, and more.
Use cases
Three Steps to Navigate Phalcon
Frequently Asked Questions
How does Phalcon operate technically?
- Phalcon continuously monitors all mempool and on-chain transactions for malicious activities, including transactions, proposals, and contracts.
- Transactions are categorized into three risk levels: Attack, Suspicious, and Regular, complemented by user-defined trigger rules.
- When transactions meet specified risk levels and trigger rules, predefined response actions (i.e. blocking transactions) are automatically triggered, utilizing an exclusive gas-bidding strategy to speed up these transactions and frontrun attacks.
What is the false positive rate of Phalcon?
During Phalcon's internal operations over the past two years, 99% of reported attack transactions have been verified as true attacks.
Even more, users can enhance precision by customizing their own trigger rules, such as changes in token amounts, prices, key variables, sensitive events, and function invocations. An alert or action is only triggered when a transaction meets both the specified risk level and user-defined trigger rules, further minimizing false positives to the lowest level possible.
Why is Phalcon able to execute a successful front-running?
- Precise Detection in the Mempool: Phalcon accurately identifies malicious transactions in the mempool. This allows Phalcon to front-run and block the attack even before it occurs, keeping potential losses to zero.
- Exclusive Bidding Strategy: Phalcon strategically bids higher gas fees to ensure its transactions are processed before those of attackers, securing priority in execution.
What value does Phalcon offer to L2 protocols
(since L2s don't have a mempool)?
In most cases, hackers don't launch a single attack; instead, they execute multiple attacks across various chains in a short period. When the first attack transaction is recorded on the blockchain, Phalcon can detect it immediately. If an L2 protocol employs Phalcon, the system can promptly alert the team and automatically pause the protocol, limiting losses to just the initial attack.
How can l configure front-running in the Phalcon system?
- Phalcon initiates frontrunning by automatically sending a blocking transaction through EOA wallet or multi-sig wallets upon detecting an attack.
- EOA Wallet: Users need to use their EOAs to pre-sign 'blocking' transactions and upload them to Phalcon.
- Multi-sig Wallet: Multi-sig Wallet: Phalcon creates a custom module for Safe{Wallet} that bypasses the standard multi-signature process. This allows a user-designated EOA to automatically sign the 'blocking' transaction. To use it, users just add the module's address to their Safe{Wallet}.
Can Phalcon monitor the deployment of malicious contracts?
Yes. Phalcon utilizes AI algorithms to preemptively identify malicious contracts even before attack transactions are initiated.
In scenarios where destination addresses are passed as parameters, traditional fuzzing techniques fall short. Phalcon overcomes this by detecting malicious activities during both the smart contract deployment and attack transaction execution phases.
Can Phalcon monitor private mempool transactions?
Private mempool transactions are undetectable, even by Phalcon. However, once such an attack is executed, Phalcon can immediately detect it, alert the protocol team, and automatically initiate a blocking transaction. Given that over 90% of attacks involve multiple transactions, Phalcon plays a crucial role in helping users prevent further losses after the initial one.
We are also in the process of collaborating with private mempool providers who have the compliance requirements to exclude attack transactions.
Which chains does Phalcon support?
Currently, Phalcon supports Ethereum, BSC, Arbitrum, and Merlin, with support for other L1/L2 chains also in our pipeline. If you would like to accelerate Phalcon's support for a specific chain, please contact us at contact@blocksec.com.
What is Phalcon's pricing and subscription process?
Is any trial available?
- Pricing & Subscription: Phalcon is a SaaS platform. Afterlogging in, users can view pricing for different features and subscribe directly. For any questions, feel free tobook a demowith our security experts who will address your concerns.
- Trial: Join the Phalcon Virtual Experience Journey to see how Phalcon blocks attack transactions! Complete the journey to receive a coupon for a 7-day trial of Phalcon for just $9, compared to the regular price of $4,600 per month.
Phalcon Toolset
Phalcon Explorer
Dive into Transactions to Act Wisely
A virtualization tool that facilitates the analysis of complex transactions, essential for understanding attack transactions.
Learn morePhalcon Fork
Collaborative testing on mainnet forked chains
A testnet designed for collaborative development and public-mode testing.
Learn more